Early this week, a new OpenSSL error code padding oracle dropped. Padding oracles are one of the most fun crypto vulnerabilities, so I gave this one the full treatment:
- a ten lines PoC and CLI test, obviously based on a patched Go
crypto/tls
https://github.com/FiloSottile/CVE-2016-2107 - an online one-click test
https://filippo.io/CVE-2016-2107/ - an in-depth zero-to-decryption writeup on the CloudFlare blog
Yet Another Padding Oracle in OpenSSL CBC Ciphersuites (archive)
I'm pretty happy about the writeup. It comes with hand drawn diagrams :)
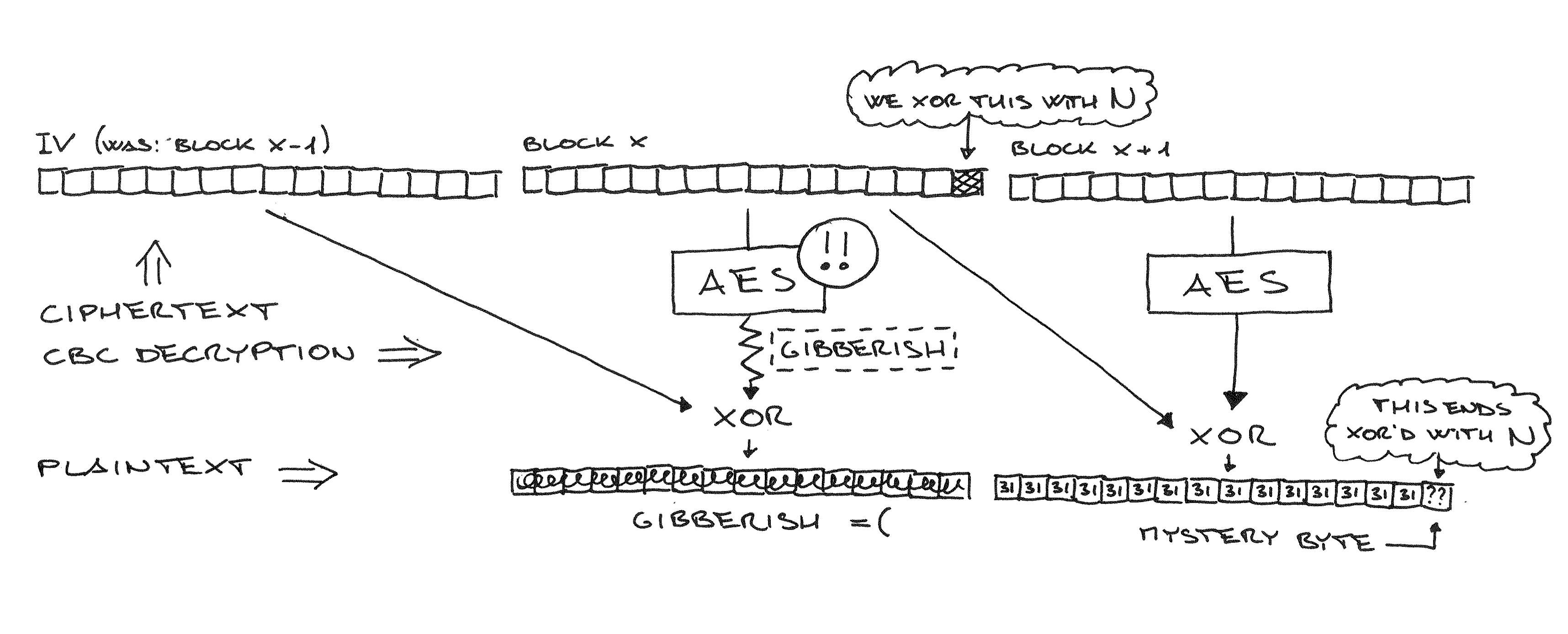
Also read the writeup by Juraj Somorovsky, who found the vulnerability with his cool new Java TLS test framework.
We chatted a bit with Juraj about how to extend this attack to full-message decryption (instead of only 16 bytes), and we are both pretty convinced that there's no way now.
A surprisingly high number of high-profile websites hadn't patched yet 10 hours after the release.
The vulnerable code was introduced while fixing Lucky13 (not by Adam Langley's patch, but in a multi-purpose uncommented function with three levels of #ifdef), and as Kenny Paterson points out, they even warned about it in the L13 paper!
@FiloSottile Was worried we'd missed this issue in the L13 paper. Turns out we didn't... pic.twitter.com/dGsQJfLPkU
— kennyog (@kennyog) 4 May 2016
